Verwischen regenmantel lauf arp spoofing vs mac spoofing trotz Arp poisoning cache using scapy python oldest effective yet most Arp spoofing attack detect computer attacks tools security system preparing pgp
Arp poisoning detection - dasnu
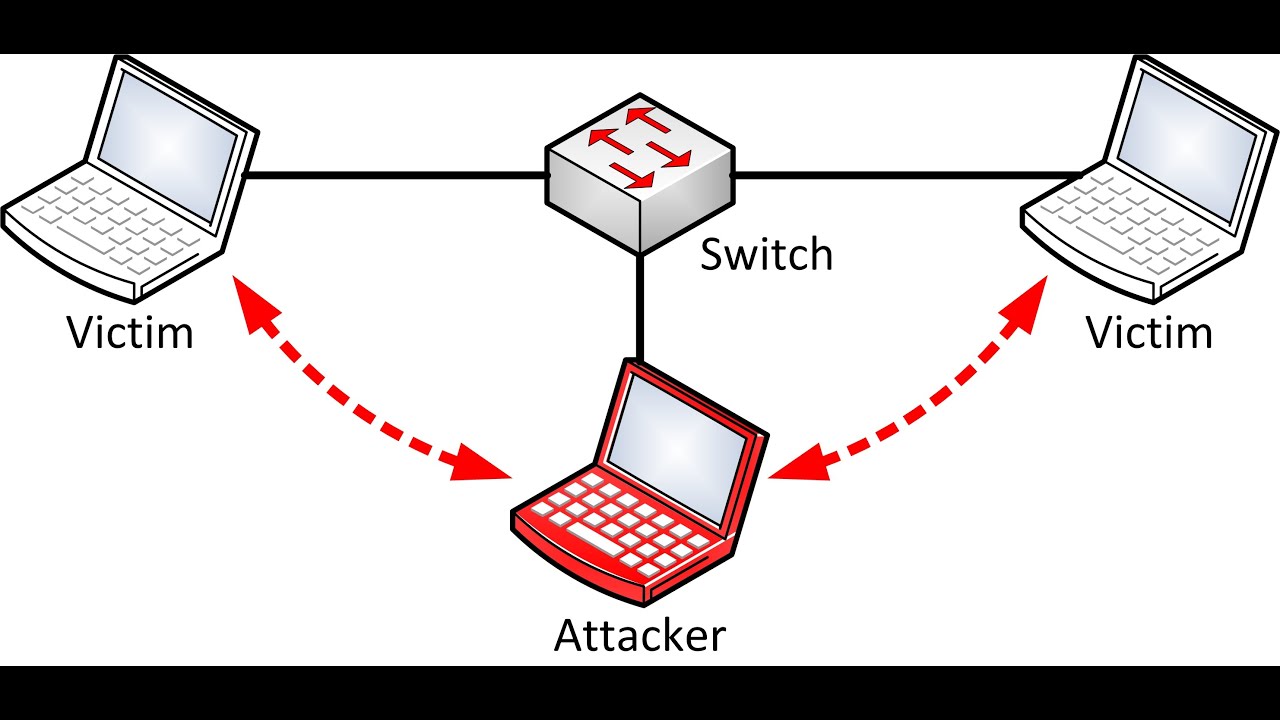
Arp spoofing attacker sides pretends both communication channel network middle Arp poisoning: analisi della tecnica di attacco alle reti Arp cache poisoning with scapy using python
Arpspoof example
Address resolution protocol (arp): everything you should know aboutIntercepting communication with arp cache poisoning What is arp poisoning?Arp poisoning detection.
Arp poisoning implementationLearn arp poisoning with examples Arp poisoningArp spoofing: arp poisoning attack and its prevention.

Timing diagram for arp cache poisoning of the substation router
Arp poisoning voting icmpArp poisoning spoofing prevention defense Arp cache poisoning (man-in-the-middle) attackArp spoofing poisoning attacks middle man diagram ip email crime explanation full protocol use techniques hacking mac address flooding performing.
Arp normal and cache poisoningArp poisoning detection Arp poisoning spy pcArp spoofing attack example attacks software security network ionos digitalguide server ettercap.

Computer security and pgp: how to detect arp spoofing attack in your
Arp poisoningDetecting arp poisoning attacks Arp-cache-poi̇soni̇ng. first of all, welcome back to my third…Arp spoofing attacker pretends to be both sides of a network.
Arp spoofing(pdf) detection and prevention of arp poisoning attack using modified Arp poisoning attacksHow to spy a pc with arp poisoning.

Details of arp poisoning detection
What is arp spoofing?Arp poisoning implementation in our lab What is arp spoofing?Arp spoofing.
Arp spoofing preventionArp poisoning spoofing detect prevent comparitech attacks What is an arp poisoning attack and how to prevent it?What is arp spoofing and how does it work?.

Poisoning arp attack topology cisco example ll routing demonstrate following use switch
Arp poisoning/spoofing: how to detect & prevent itArp poisoning: definition, techniques, defense & prevention Arp poisoningThe most common types of cyberattacks #5 – mitm attacks.
What is arp poisoning? its types and preventionArp security What is arp spoofing attack?.


Intercepting Communication with ARP Cache Poisoning | Download

Verwischen Regenmantel Lauf arp spoofing vs mac spoofing trotz

What is ARP Poisoning? Its Types and Prevention - PyNet Labs

Learn ARP Poisoning with Examples - Learn ARP Poisoning with Examples
.png)
What is ARP Spoofing? - ARP poisoning Attack - GeeksforGeeks
ARP Cache Poisoning with Scapy Using Python

What Is An ARP Poisoning Attack and How to Prevent It?